"Preparation is everything" (see reference 1 below). If you have done the proper preparation up front, avoiding or recovering from a cyberattack will be more likely.
The Importance of Preparation
Preparation for when (not if) your organization gets targeted by a cyberattack is one of the most important aspects of cybersecurity defense. As seen in the Critical Insight Cybersecurity as a Service infographic below, from the seven core areas that need to be in any comprehensive cybersecurity strategy, four are activities that are direct preparation to prevent attacks, and another is long-term preparation for regulatory compliance.
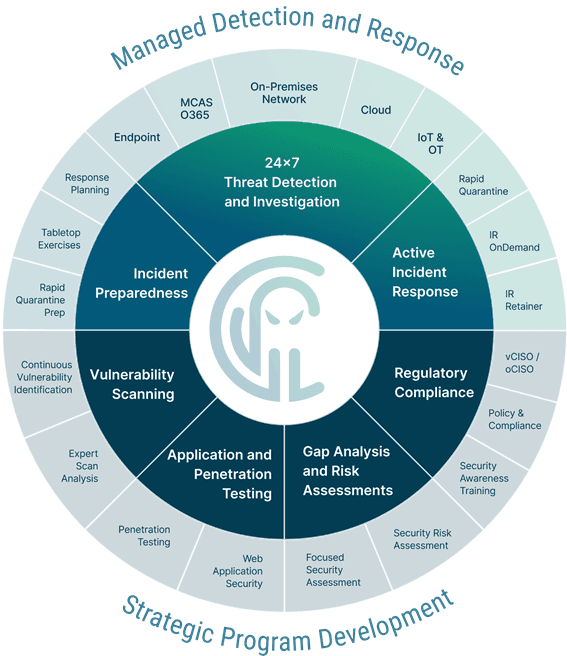
Prepare, Detect, Respond
As you'd guess, outcomes tend to be better if your response to any given set of circumstances gets shaped by prior training and thinking. In cybersecurity defense, this preparatory work falls into the following core areas.
Risk identification and mitigation
When building a cybersecurity defense strategy, "you can't defend what you don't know" is a frequently used phrase. For most organizations the resources they have available to spend on cybersecurity protection will be finite, and it is vital that they are used in the best way possible to maximize return on investment.
If funds are to get used well, there must be an overall picture of the current cybersecurity situation. The following methods deliver this overall picture:
- Audit of current systems - A comprehensive audit of everything that is part of the IT deployment is the first step. This should identify all the servers, network equipment, endpoint devices, IoT devices, users, and often forgotten devices like printers attached to the network, even if they are devices that are only connected intermittently. In areas like healthcare and manufacturing, this audit needs to identify all networked specialist equipment. If it's on the network, it is a potential weak spot for cybercriminals to exploit. Don't be surprised if an audit reveals things you didn't know about. This is normal, and why this step is vital.
- Categorize systems and data - Once all the systems that connect to the network are known, they and the data they hold should be categorized and ranked in order of sensitivity and importance as part of a risk assessment. It's crucial that the most sensitive data (such as patient records) or any other sensitive data gets identified so those systems can be evaluated for vulnerabilities in preference to other less important ones (remembering that resources are finite, and choices are needed).
- Vulnerability scanning and penetration testing - Scanning the systems on the network for known vulnerabilities (starting with the ones that have the most sensitive or important data) and also performing complete external penetration testing of the network and systems should be done. The data that this results in can be used to identify what steps are needed to plug security gaps.
- Create and follow an improvement plan - Once vulnerabilities are known, cybersecurity experts should create a plan to plug the gaps. This plan needs to be realistic and address the most critical issues first and then address other less critical ones on a doable timeline. Trying to handle everything at once is a recipe for failure. As mentioned above, resources are finite (people and funding), so the plan must respect this reality.
After the risks are known and a plan put in place to address them, there needs to be additional planning and preparation for when a cyberattack happens.
Response Planning
Every organization should work under the assumption that that will be targeted by cyberattacks and that some of the attacks will breach defenses. For this reason, there needs to be planning so everyone knows what to do when an attack happens.
Note that this planning is separate and different from the improvement plan discussed above. The latter is to fix issues over time and improve the cybersecurity posture. In contrast, the response plan details what needs to be done when an attack happens. Incidentally, 24x7 network monitoring is vital for cybersecurity. It's not part of the preparation except for the initial decision on how you will deliver 24x7 monitoring.
An incident response plan (IRP) that is detailed and that everyone is familiar with so they can react quickly (close to instinctively) can be the difference between a cyber incident being minor or catastrophic. As our response team likes to say, "When you're in the middle of a fire, you don't want to be reading the instructions for the fire extinguisher!"
A comprehensive incident response plan should contain the following elements and associated activities (see ref 3 for more detail):
- Documented procedures, policies, and actions. The documents should include sections for everyone from staff using endpoint devices to dedicated cybersecurity staff and designated contacts for any cybersecurity as service contracts. The detail for different types of staff will vary. For end users, their sections should detail what to do if they suspect something suspicious and how to report (without adverse consequences) if they think they have disclosed information or visited a malicious website. There should be more detailed technical procedures for other classes of employees, such as managers and IT and security teams. The plan should have dedicated playbooks matching different incident types — ransomware, DDoS, data breach, etc.
- Training and tabletop simulations should be periodic and regular. As with the fire extinguisher analogy quoted above, you don't want people to be reading the response plan when an incident is happening. Teams need to perform simulated tabletop run-throughs of typical scenarios so that everyone knows how to respond quickly to mitigate any damage that could flow from a cyberattack. Participants should use the playbooks for each incident type to ensure everyone knows how to react to any incident.
- Ongoing updating of the response plan should occur. Organizations are not static. As they change over time, their cybersecurity needs will also change, and the plan will need updating regularly. The timing of the reviews and updates to the response plan is often tied to the periodic training and tabletop exercises, as this is usually when new security gaps or organizational changes come to light.
Regulatory Compliance
A broader aspect of preparation is compliance with regulations that pertain to the industry an organization operates within. Regulations can be from Government (HIPAA or CCPA, for example) or industry-led (like PCI DSS). Coupling requirements for compliance with the general cybersecurity planning makes sense, as there will be considerable overlap between the internal cybersecurity needs and the external regulations. Coupling them saves effort and resources, and each strand feeds into and strengthens the other.
How To Respond After an Attack
While preparation is essential and has to be detailed and ongoing, there is no such thing as 100% protection from cyber criminals. The threat landscape is constantly changing. New vulnerabilities get discovered weekly, and bad guys usually exploit them before organizations can apply fixes to their systems.
Bottom line? Every organization should assume they will be victims of a successful cyberattack.
When an incident is detected (again - you need 24x7 monitoring), all of the planning and tabletop exercises & training outlined above come into their own. When an incident is in progress, the response speed is crucial. The goal of the initial response should be:
- Contain the threat so it can't spread and impact other IT systems. This is especially true for ransomware and other destructive malware.
- Communicate to all staff what is happening with instructions on what they should and shouldn't do. Not everyone will remember their training or the playbooks.
- Remove attackers and their software from any systems they have compromised.
- Return compromised systems to a pre-attack state.
- Perform an analysis of the incident to discover how the attackers gained access.
- Update Improvement and Incident Response plans based on insights gained from the analysis of the successful attack to prevent others from using the same attack method in the future.
- As required, communicate what happened and the outcome to clients, insurance providers, law enforcement, and regulators.
Conclusion
Is preparation everything when it comes to cybersecurity defense? No, it's not. As the cybersecurity as a Service wheel shows, a complete strategy also includes 24x7 detection and response capabilities.
But, if you haven't done the prep to support your active monitoring and response efforts, then your outcomes will be worse than you hope.
Critical Insight can help you prepare and defend in real-time and improve your defensive posture over time. Use the form below to discuss enhancing your preparation and defense.
References
Business Insider: David Robinson Letter To My Younger Self - https://www.businessinsider.com/david-robinson-letter-to-my-younger-self-2016-11
Critical Insight Services - https://www.criticalinsight.com/services
Critical Insight: Incident Preparedness https://www.criticalinsight.com/services/incident-preparedness